AWS Powers Your Cloud, Prophaze Keeps It Unbreakable
- AWS-Native WAAP
- API-first protection
- Auto-scalling security
- Cloud-native integration
- App-layer protection
Why Native AWS Controls Alone Can’t Stop Modern Application Threats
Security Leads
Prophaze MeshGuard Fix
DevOps / Platform Teams
Prophaze MeshGuard Fix

Business / CTOs
Prophaze MeshGuard Fix
From Fragmented AWS Security to Unified WAAP in 3 Steps

Step1
Connect Prophaze to AWS
Step1
Connect Prophaze to AWS
Step2
Auto‑Discover & Analyze
Step2
Auto‑Discover & Analyze
Step3
Activate Adaptive Defense
Step3
Activate Adaptive DefenseSecurity Outcomes That Scale with AWS Cloud Platform
Substantial reduction in OWASP Top 10 and API Top 10 risks across CloudFront, ALB, API Gateway, and EKS‑based workloads through continuous discovery and adaptive protection.
Robust L7 defense against bots, credential attacks, and scraping—preserving seamless experiences for legitimate users on web and mobile channels.
Uninterrupted performance during large‑scale and multi‑vector DDoS events, supported by AI‑driven L3–L7 mitigation that scales with AWS elasticity.

Unified WAF, API, and bot policies consistently enforced across AWS accounts, regions, and environments—including containerized, serverless, and VM‑based deployments.
Centralized visibility and investigation-ready analytics for AppSec and DevSecOps teams, enabling faster incident response and cleaner signal‑to‑noise ratios.
Streamlined compliance alignment with PCI‑DSS, GDPR, SOC 2, and ISO 27001 through consolidated, audit‑ready reports layered on AWS’s secure infrastructure.
Integrated for AWS Cloud-Native EnvironmentsEnvironments




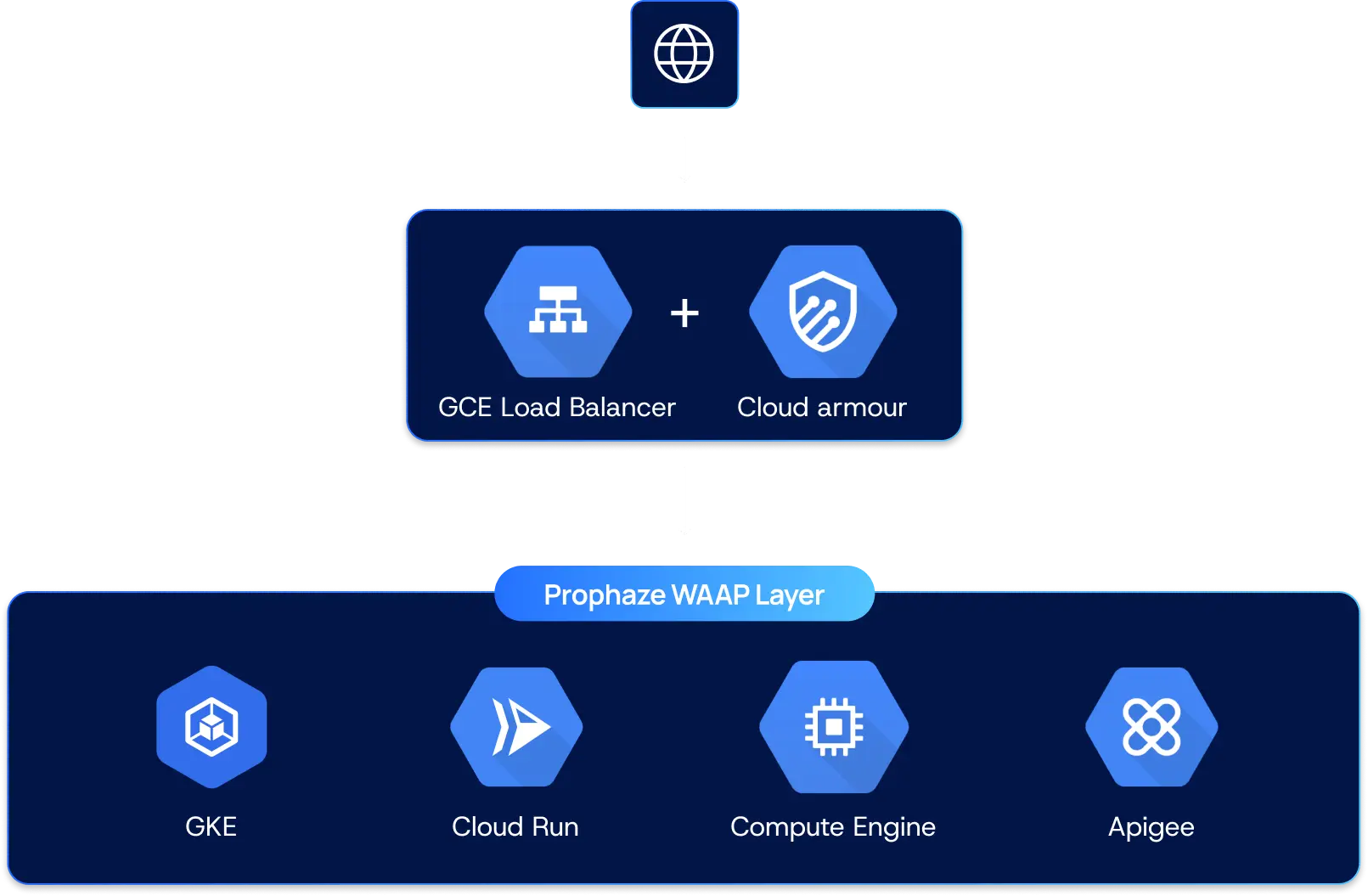
Security That Moves at AWS Cloud Speed

- Native fit with Infrastructure as Code (Terraform, CloudFormation, CDK) and AWS resource models—no brittle, per‑ALB rule tweaking.
- Zero‑downtime protection and policy rollouts across regions during autoscaling, blue‑green, or multi‑AZ failovers.
- Predictable WAAP performance and consistent response times even during unexpected traffic surges or AWS scaling events.

- 24/7 automated threat monitoring integrated with AWS CloudWatch, GuardDuty, and third‑party SIEM/SOAR platforms.
- Role‑based dashboards with deep WAF, API, and bot analytics plus audit‑ready logs for incident response and compliance reviews.
- Reduced noise and false positives with behavior‑adaptive detection that distinguishes real threats from legitimate user traffic.

- Policy‑as‑code for WAF, API, bot, and DDoS protections—version‑controlled alongside app and infra code for accountability.
- Seamless hooks into CI/CD pipelines (CodePipeline, Jenkins, GitHub Actions) to test rules pre‑deployment and prevent regressions.
- Git‑integrated workflows and AWS‑native automation that shift security left—without slowing code delivery or release agility.
Centralized Security Insight Across Your AWS Estate

Understand who is calling which applications and APIs, from where, and through which AWS edges—via correlated insight across WAAP, API, and DDoS telemetry.

Detects abnormal traffic and attack patterns in seconds using intelligent baselines, anomaly‑driven alerts, and precise distinction between noise and real threats.

Investigate and respond faster with full request context—headers, rule hits, impacted APIs, and historical behavior—all mapped to AWS environments and services.

Share intuitive dashboards and reports across teams with seamless exports into CloudWatch, GuardDuty, AWS Security Hub, and leading SIEM/SOAR platforms.
Integrations
AWS-Native WAAP Capabilities Legacy WAFs Can’t Match
Threat Protection
- Comprehensive OWASP Top 10 coverage for web apps and APIs—defending against SQLi, XSS, RCE, broken authentication, and business logic abuse across CloudFront, ALB, and API Gateway.
- API abuse defense with schema‑aware validation, rate limiting, sensitive data inspection, and robust protection for OWASP API Top 10 risks across internal and external APIs.
- Alwayson L3–L7 protection combining adaptive WAF, DDoS mitigation, and behavior‑based bot management—keeping AWS workloads stable through volumetric and targeted attacks. .
Operations & Governance
- Centralized policy control for WAF, API, bot, and DDoS protections across multiple AWS accounts, regions, and architectures (EKS, ECS, Lambda, EC2).
- Role‑based dashboards with AWS Identity and Access Management (IAM) integration and rich audit logs for clear visibility and compliance readiness.
- Environment‑aware controls to isolate dev, staging, and production configurations with safe promotion paths and scoped permissions for critical workloads.

Automation & Integration
- IaC‑ready APIs and templates for seamless integration with Terraform, CloudFormation, and AWS CDK pipelines—ensuring consistent, automated deployments.
- Native telemetry exports to CloudWatch, GuardDuty, AWS Security Hub, and third‑party SIEM/SOAR tools for automated threat correlation and response.
- Simulation and dry‑run modes to test rule updates, rate limits, and bot policies against live AWS traffic before applying enforcement in production.

Proven WAAP for Mission-Critical AWS Cloud Workloads