Microsoft Azure Runs Your Business, Prophaze Keeps Its Apps and APIs Unbreakable
- Azure WAAP shield
- OWASP Top 10 blocker
- Azure-Native security
- Zero-trust enforcement
- Shadow API discovery
Why Native Azure Controls Alone Can’t Keep Up With Modern App & API Attacks
Security Leads
Prophaze MeshGuard Fix
DevOps/Platform
Prophaze MeshGuard Fix

Business/CTO
Prophaze MeshGuard Fix
From Fragmented Azure Security to Locked-Down in 3 Steps

Step1
Connect Prophaze to Azure
Step1
Connect Prophaze to Azure
Step2
Auto-Discover & Baseline
Step2
Auto-Discover & Baseline
Step3
Activate Active Defense
Step3
Activate Active DefenseSecurity Outcomes That Scale with Azure
Organizations running critical workloads on Azure use Prophaze to achieve:
Dramatically lower exposure to OWASP Top 10 and API-specific risks across App Service, AKS, Front Door, and APIM.
Effective L7 protection against bots, credential stuffing, and scraping without blocking legitimate users.
Stable performance and uptime during volumetric and application-layer DDoS spikes, backed by 99.99%-level availability.

Consistent WAF, API, and bot policies enforced across regions, subscriptions, and mixed Azure architectures.
Deep visibility into application and API traffic, with threat analytics that SecOps can take action, not just log.
Easier compliance alignment with PCI-DSS, GDPR, and SOC 2 through centralized, audit-ready security reporting.
Built Real-World Azure Architecture




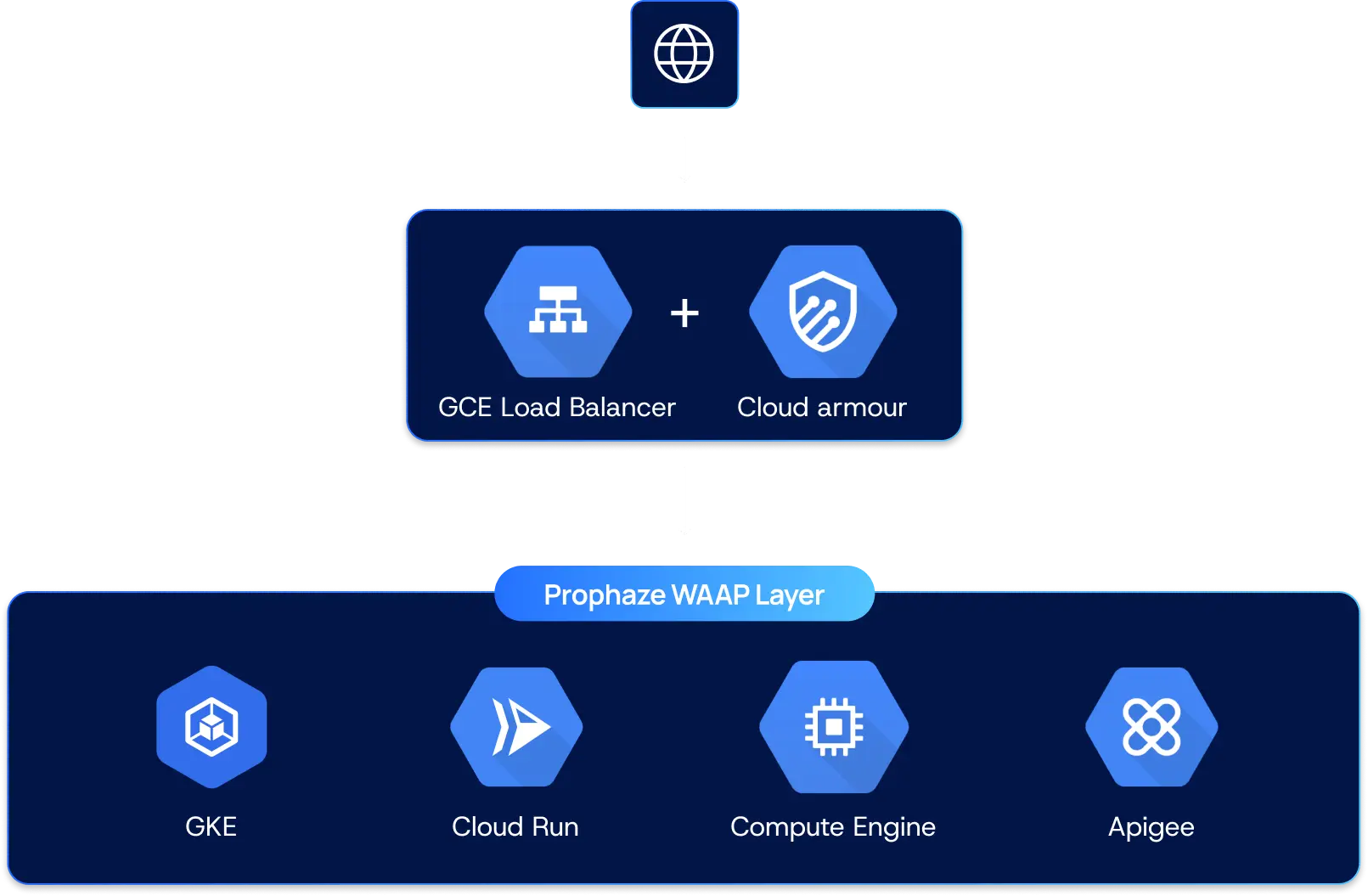
Security That Moves to Azure Speed

- Native fit with Azure Resource Manager, templates, and IaC—no brittle custom rule scripts to maintain.
- Zero-downtime updates and policy rollouts across regions and subscriptions as apps autoscale or shift traffic.
- Predictable WAAP performance that stays sta

- 24/7 threat monitoring with automated response playbooks and integrations into Microsoft Sentinel and other SIEM/SOAR platforms.
- Role-based dashboards, rich WAF and API telemetry, and audit-ready logs for investigations and compliance.
- Fewer noisy alerts and false positives through behavior-aware rules that cut WAF alert fatigue.

- Policy-as-code for WAF, API, bot, and DDoS controls, versioned alongside app and infra code.
- CI/CD hooks to test security policies before promotion, keeping pipelines fast and safe.
- Seamless integration into Azure DevOps and Git-based workflows so teams can “shift left” without slowing releases.
Centralized Security Insight Across Azure Estate

Understand who is calling which applications and APIs, from where, and through which Azure edges, with correlated views across WAF, API, and DDoS telemetry.

Detect abnormal behavior and attack patterns quickly with ML-style baselines, anomaly-aware alerts, and clear separation of noise vs. real incidents.

Respond to incidents with full context—request traces, rule hits, and impacted endpoints—so action is fast and defensible.

Share intuitive dashboards and reports across security, cloud, and leadership teams using exports into Microsoft Sentinel, Azure Monitor, and SIEM/SOAR tools.
Integrations
Azure-Native WAAP Capabilities Legacy WAFs Can’t Match
Threat Protection
- OWASP Top 10 coverage for web apps and APIs: SQLi, XSS, RCE, broken auth, injection, and business logic abuse across Azure Front Door, App Gateway, App Service, AKS, and APIM.
- API abuse defenses: schema-aware validation, rate limiting, data-leak controls, and protections tuned to OWASP API Top 10 risks.
- Always-on L3–L7 protection combining app-layer WAF with adaptive DDoS and bot mitigation to keep services responsive under attack.
Operations & Governance
- Centralized policy management for WAF, API, bot, and DDoS controls across regions, subscriptions, and mixed Azure architectures.
- Role-based dashboards with Azure AD SSO for security, cloud, and product teams, plus rich audit logs for investigations.
- Environment-aware controls for dev, staging, and prod with safe promotion paths and configuration isolation.

Automation & Integration
- Policy-as-code and IaC-friendly APIs for integrating Prophaze into ARM/Bicep/Terraform pipelines and Azure DevOps.
- Native hooks for exporting telemetry to Azure Monitor, Microsoft Sentinel, and external SIEM/SOAR tools for automated response.
- Simulation and dry-run modes to test rule changes and rate-limits before enforcing them in production.

Proven WAAP for Mission-Critical Azure Workloads