Layer 7 DDoS Attacks Rising, Prohaze Shields Every Request
- Real-time L7 defense
- Behavioral traffic baselining
- Captcha-free bot filtering
- AI smart rate limiting
- Live attack visibility
- Unified deployment Cloud / on‑prem / K8s
Application-Layer Chaos Rising,
Precision Defense Restores Control

Application-layer floods that mimic real traffic.

Low-and-slow attacks that exhaust connections silently.

Bot-driven API calls that overload backend logic.
Microservice exposure turning internal paths into attack surfaces.
App-Facing Edge Exposed,
Dynamic Defense Guard Every Call

AI-powered detection that identifies HTTP floods, Slowloris, and complex low‑rate DDoS behaviors in milliseconds.

Deep behavioral inspection that separates real users from attacker‑generated traffic.

Adaptive rate limiting that learns live traffic baselines and automatically controls abusive spikes.

Built‑in bot and API abuse mitigation to stop blended application‑layer attacks at the edge.

Always‑on, fully automated mitigation running natively inside your Kubernetes and cloud environments.

Compliance‑ready controls aligned to OWASP guidance and modern DDoS best practices.
How Prophaze DDoS Engine Stops Layer 7 Attacks in Real-Time
Traffic baselining & anomaly scoring
Learns normal HTTP and API patterns per route, tenant, and cluster, then flags abnormal spikes, bursts, and request types as soon as they deviate.
Behavioral DDoS detection
Correlates request frequency, headers, methods, and response behavior to distinguish real users from scripted floods and low‑rate, connection-draining attacks.
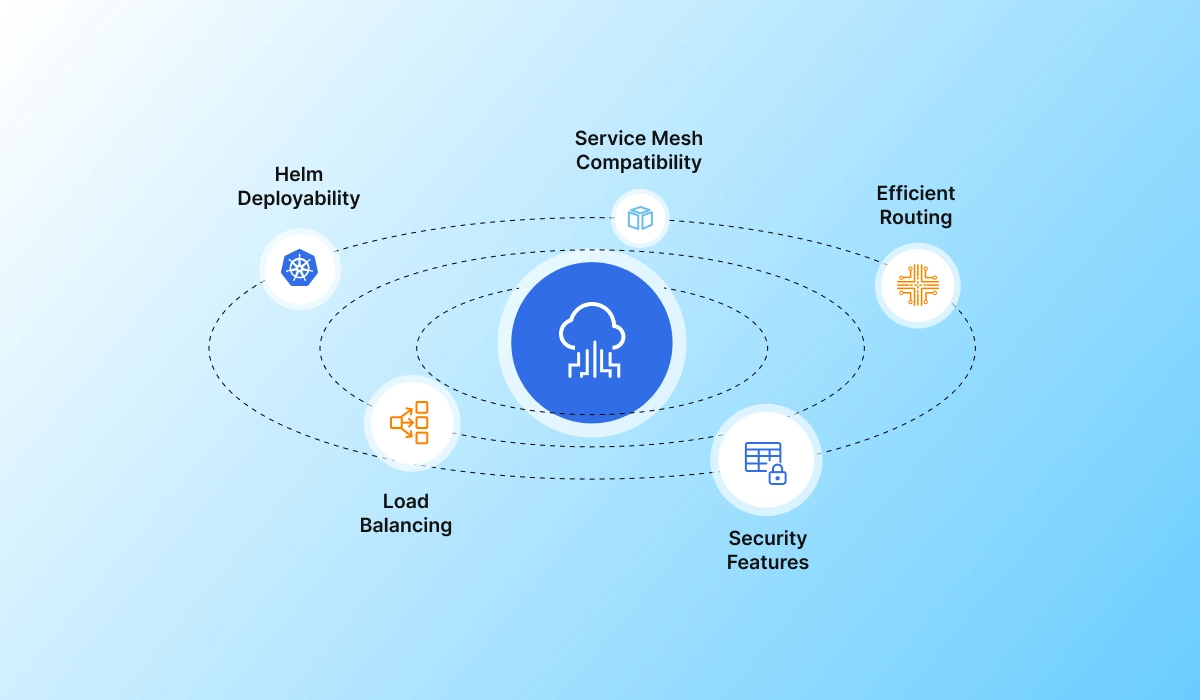
Kubernetes‑native enforcement
Runs inline with your ingress so mitigation happens closest to the source, scaling automatically with your services and clusters.

Prophaze
DDoS Protction
Smart rate limiting at the edge
Applies dynamic limits by IP, token, route, and method so abusive sources are throttled or blocked without touching legitimate user flows.
Bot and API abuse filtering
Uses reputation, fingerprinting, and protocol validation to drop malicious botnets and noisy API calls before they overload backend services.
Geo, ASN, and IP controls
Surfaces where attack traffic originates and lets teams clamp down on hostile regions, networks, or ranges without disrupting priority markets.
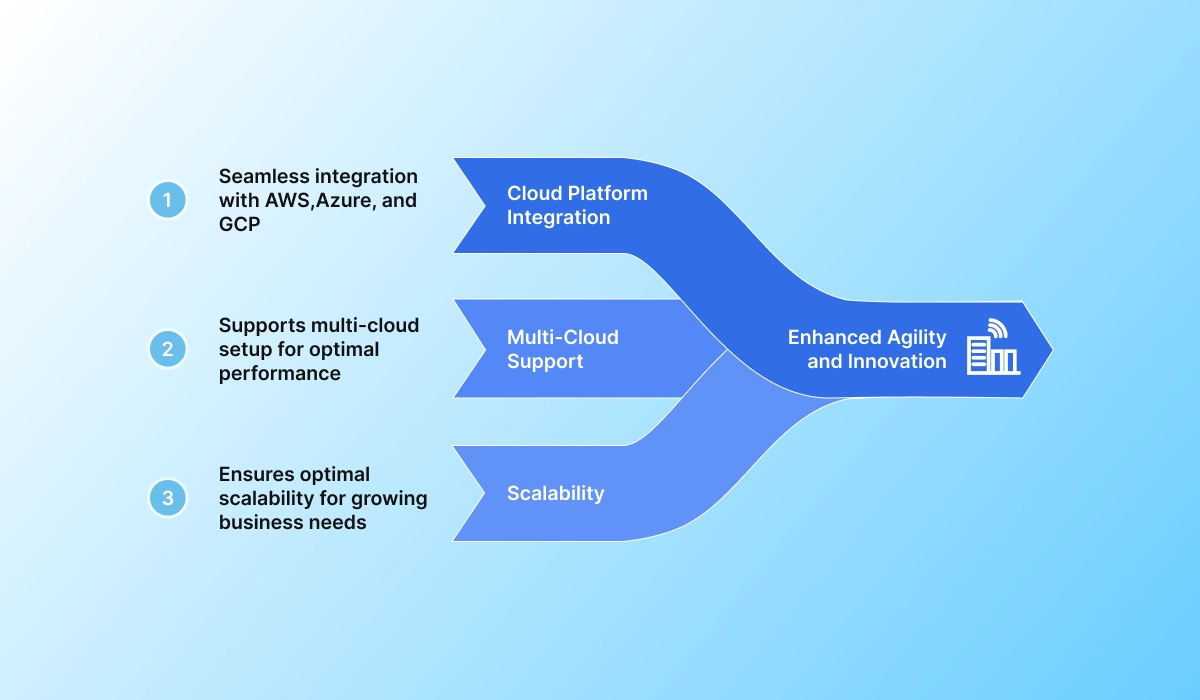
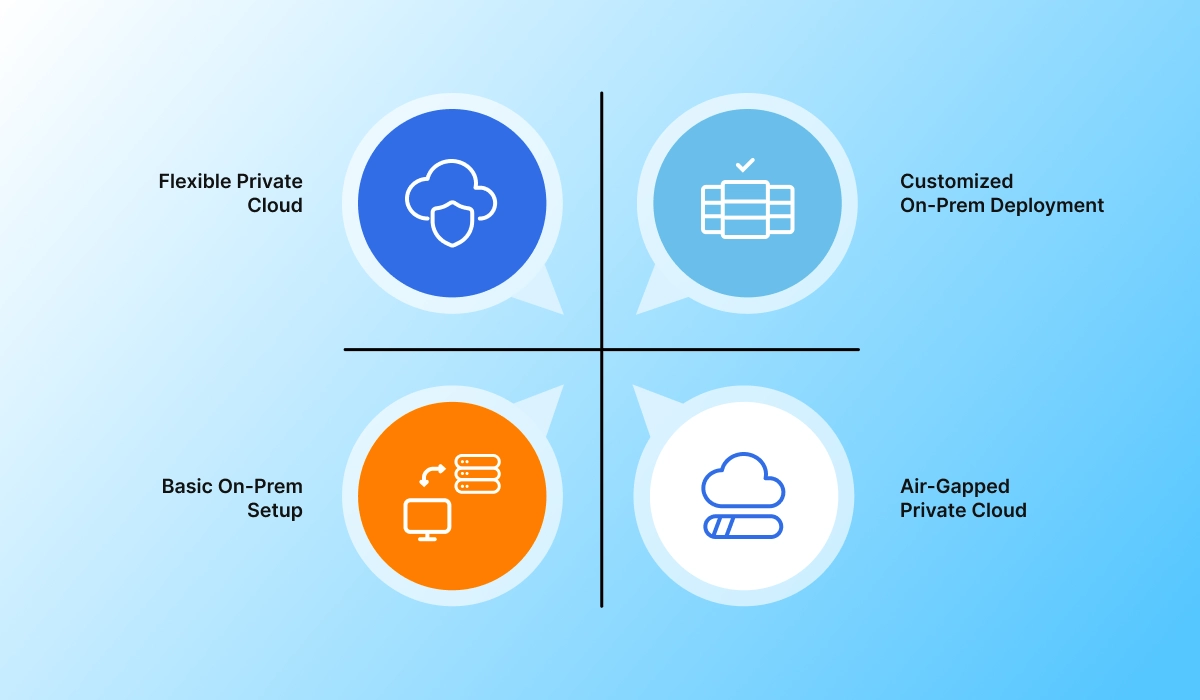
Seamless Deployment Across Any Environment
From Outage Firefighting to
Predictable Uptime in Three Clear Steps
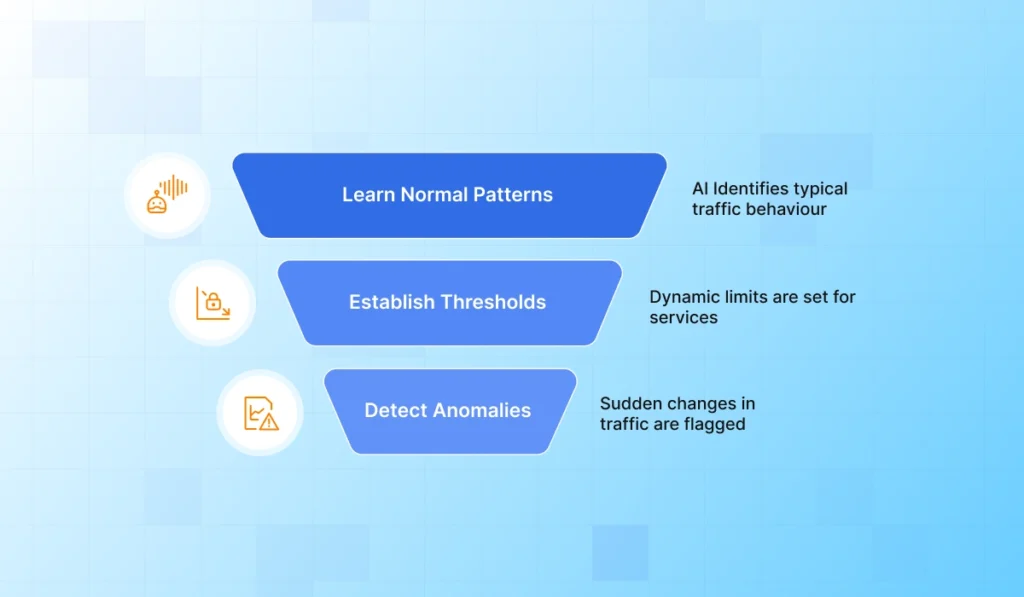
Discover & baseline real demand
- Automatically learn normal traffic patterns for every app, API, and critical route so you know what “healthy” really looks like.
- Establish dynamic thresholds per service and endpoint so sudden surges, anomalies, and abuse stand out instantly.
Detect live attacks & prioritize impacts
- Spot Layer 7 floods, low‑and‑slow connections, and protocol abuse in real time before they ripple into outages.
- Flag high‑risk sources and paths hitting revenue‑critical journeys—logins, search, checkout, and APIs—so teams know where to act first.
Protect experiences & mitigate instantly
- Apply adaptive rate limits, filters, and targeted blocks that automatically absorb attack traffic without touching application code.
- Preserve uptime and performance for legitimate users while the platform continuously tunes defenses against evolving DDoS patterns.

- Power & Utilities
- DDoS Mitigation
Securing Grid Operations, Billing, and Payment APIs Against Real-Time Cyber Threats with Prophaze WAAP
Talk directly with Prophaze security engineers to assess your current exposure and protection gaps.
SecOps Fighting Fire Drills,
Prophaze Turns L7 Chaos into Predictable Uptime

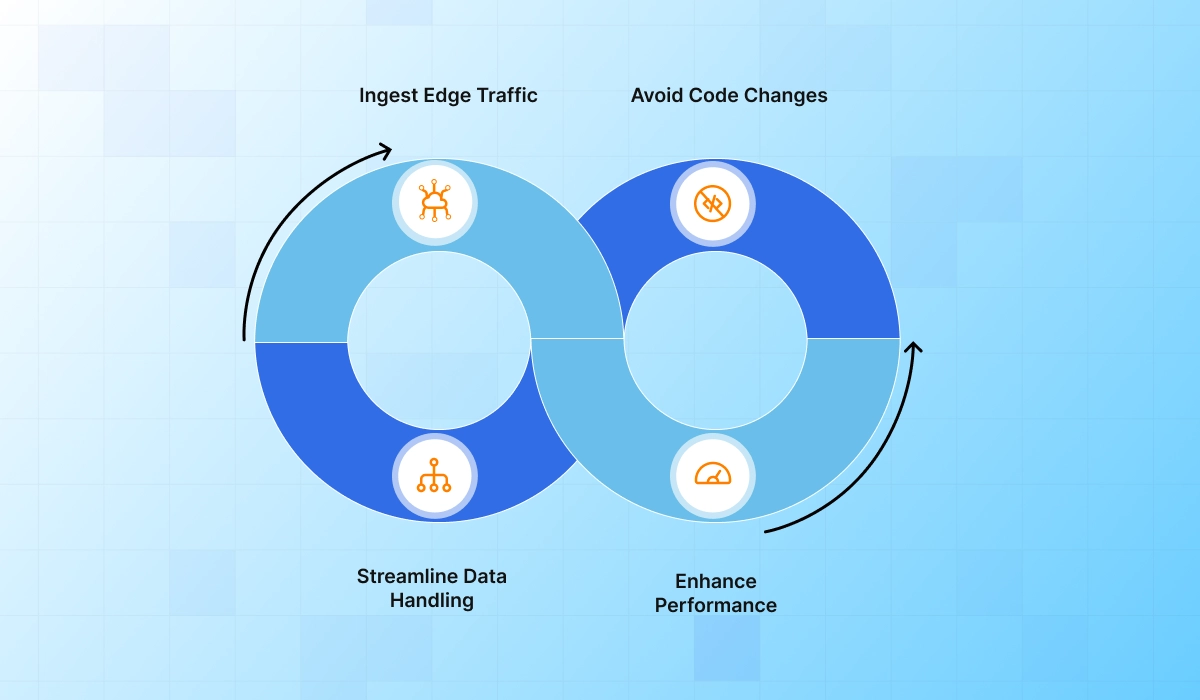
No code changes, SDKs, or application rewrites

Smart adaptive rate limiting tunes thresholds from live anomalies.

Deep protocol inspection detects spoofed headers, malformed, fragmented payloads.

Bot and API mitigation fingerprints automated requests, rogue usage.
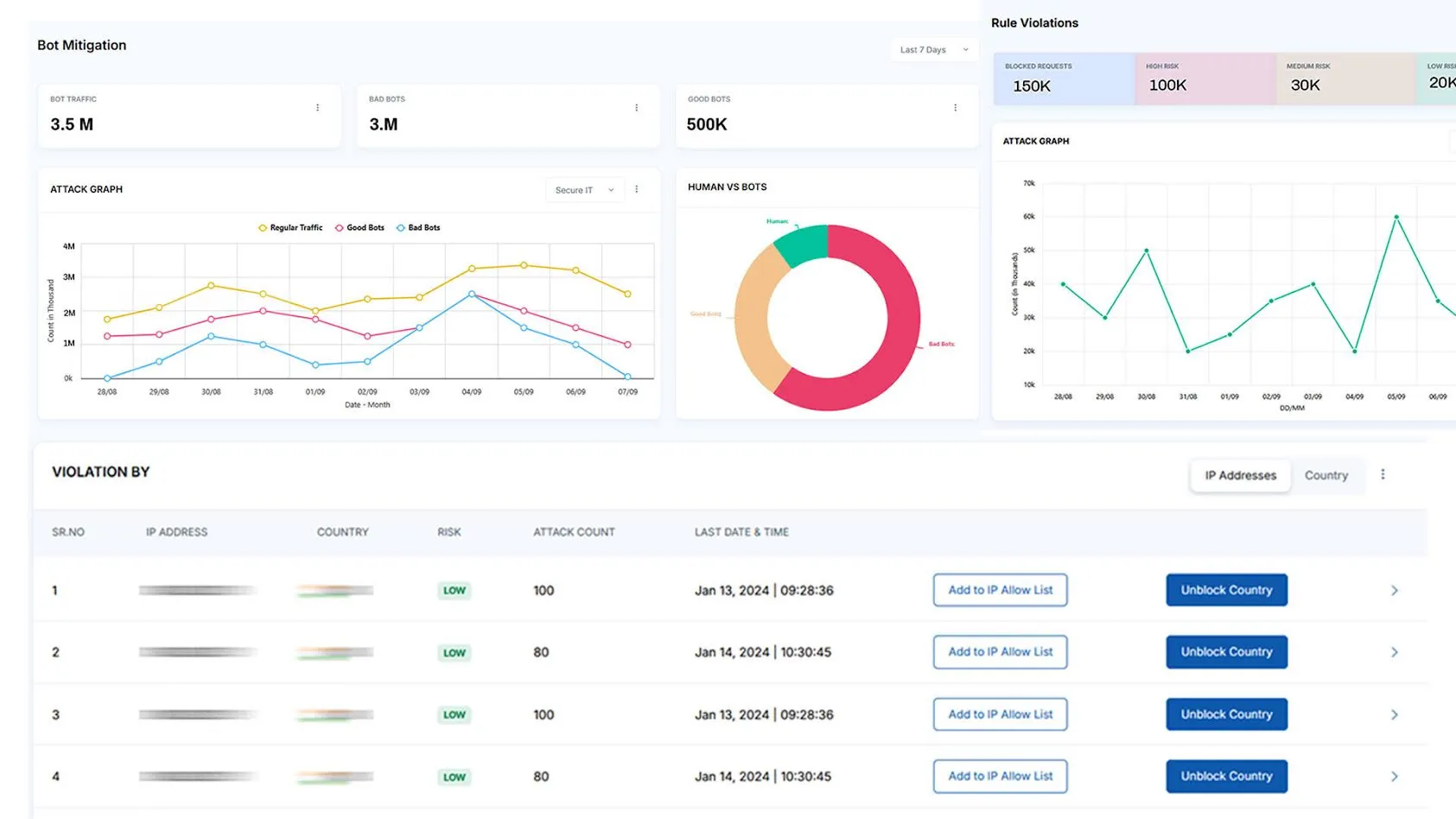
Application Attacks Hard to Track, Prophaze Shows It All in One Dashboard
Monitor DDoS attempts, surges, and anomalies in real time.
Trusted by High-Stakes Environments
Stop Layer 7 DDoS Attacks Before Availability Is Impacted
- Protect web applications, APIs, and microservices
- Maintain uptime during sophisticated attacks
- Deploy in minutes without engineering effort